Crypto Wallet Vulnerability | First Solana, Then NEAR
Not your keys, not your money. Actually, it was an undeniable fact for a long while in crypto history. However, some things have changed with the increasing interest in mobile crypto wallets and options to create wallets such as WhatsApp or SMS verifications.
Just recently we experienced a hack case in Solana. According to BlockWorks, there are some clues about the exploit but nothing is clear yet. More than 8,000 wallets were drained and Solana team blamed a mobile app named Slope!

As the hack attacks on crypto wallets and exploits of cross-chain increased, crypto people started to worry about the security that they have. To be honest, security is still a topic to be discussed for mobile and cold wallets!
The case of NEAR
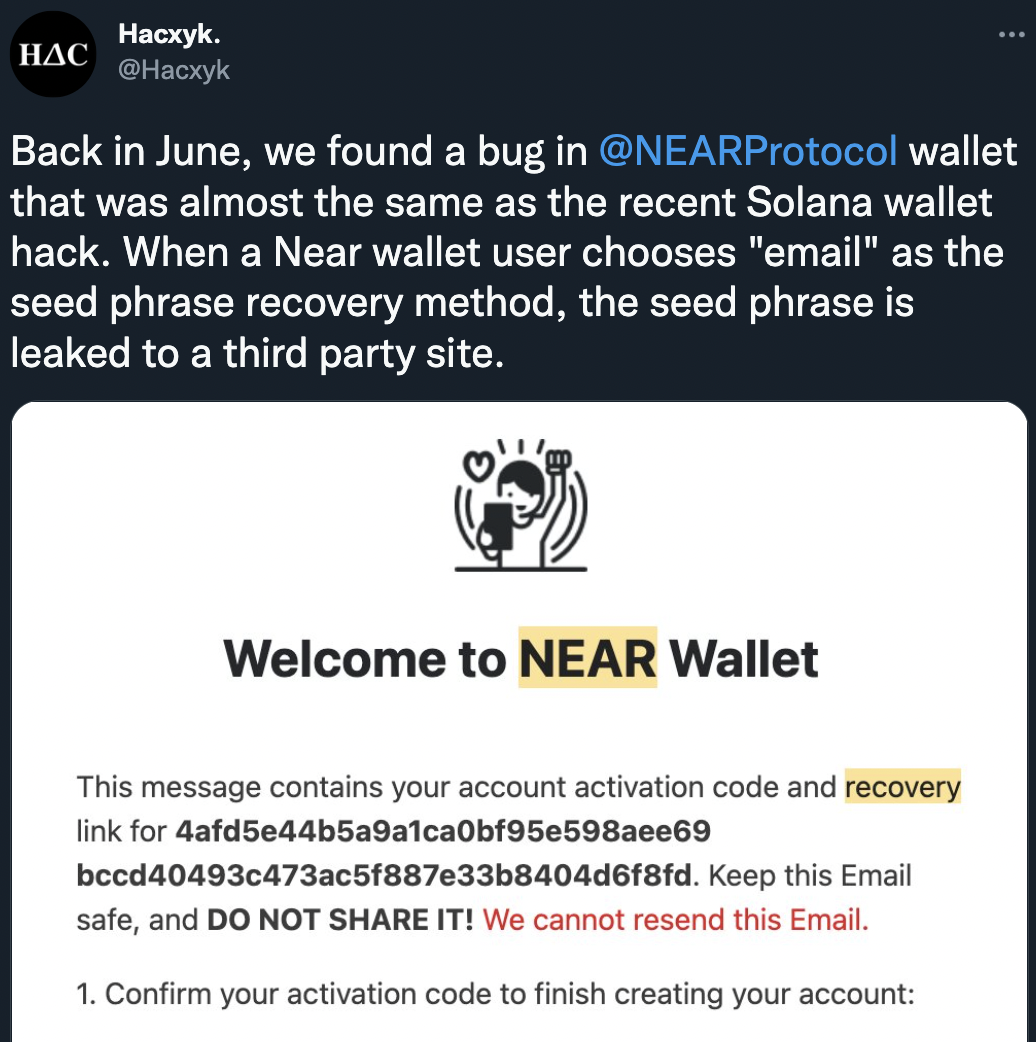
First of all, NEAR team did not share the exploit on time. Actually, the problems started in June but the team did not inform the investors while they were dealing with the issues. In other words, they deliberately hid the reality and put your money at risk.
Even a single minute is enough for you to lose everything you have. Yet, some project managers may choose not to inform you about the risks you are in.
I'm speechless!
Hacxyk shared the Near breach because of its technical similarity to this week’s Solana wallet hack. In the case of Solana, a mobile wallet called Slope had a vulnerability that enabled users’ private keys to be accessed by potential attackers. -Decrypt
It is obvious that holding your money in such mobile apps may as risky as holding them in a centralized exchange. In both ways, you have to rely on the presumed security by some parties. Not so good.
Security of Hive Wallet
As you know, Hive has a complex account key pyramid that uses different Private Keys for different purposes. Even if some parties have your Private Posting Key, all they can do is draining your voting power that recharges every single second. Yet, managing your Hive & HBD requires your Active Key to initiate transactions.
Hive Wallet:
- Requires at least your Active Key for monetary actions
- Can be accessed only via your key or open source Apps like KeyChain.
- Has Hive Savings that secures your assets for 3 Days as additional security.
If we accept these security measures as more or less blockchain standard, then how can we embrace new mobile wallets or unauditable wallets that are not stress-tested for bugs or leaks.
How Secure the Cold Wallets Are?
Cold wallets are still the best way to store your crypto. However, many people are not aware of the fact that even Ledger is not open source.
Ledger uses a unique blockchain open ledger operating system (BOLOS) that is an open-source framework. However, unlike Trezor, Ledger wallets use closed-source firmware, meaning it's not available for third parties to review or test for vulnerabilities. -Investopedia
As time passes, the security of my digital assets has become a bigger problem although there are many advancements in this area. I'm still against holding importing my private keys to mobile apps or keep my assets on the wallet provided by external apps.
For Hive assets, I stick to Hive Wallet but, for other cryptocurrencies, I only trust the wallets the core team developed or the cold wallets (with huge doubts). Unfortunately, Metamask or any extension wallet can be easily exploited with malware.
Thanks Near team for triggering the anxiety of crypto investors 🙄
Posted Using LeoFinance Beta
https://twitter.com/idiosyncratic1_/status/1555701885004386305
The rewards earned on this comment will go directly to the people( @idiosyncratic1 ) sharing the post on Twitter as long as they are registered with @poshtoken. Sign up at https://hiveposh.com.
Great Post!
!1UP
Click the banner to join "The Cartel" Discord server to know more!
You have received a 1UP from @luizeba!
@leo-curator, @ctp-curator, @vyb-curator, @pob-curator, @neoxag-curator, @cent-curator
And they will bring !PIZZA 🍕.
Learn more about our delegation service to earn daily rewards. Join the Cartel on Discord.